There is no company where the question “Give me information on all the actions with this document ASAP” doesn’t arise from time to time. It’s worse when this question is asked on list items which have been already deleted. It’s not much fun to look through the recycle bin, pull the GUID out of it and then search for this GUID in the audit logs.
HarePoint Analytics allows you to obtain this SharePoint statistics data literally in a couple of clicks, even on servers where audit logs are switched off or cut, because the product does not collect data at the level of log files, but at the level of addressing to the server.
Document audit
To see all the actions from a document, you can use the “Document usage” report. After creating it, you can apply a filter by name, mask, or document location. You can also filter for a user name to see all of that user’s actions with the documents on the site.
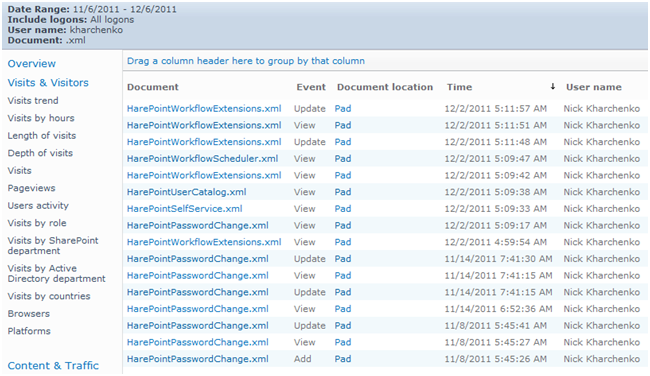
Thus, this report is suitable to investigate both user activity on the site and user interaction with documents. The product contains 15 reports for documents and allows you to get answers to any audit-related question. For example, how many and what kind of documents have been deleted in the past week, and from what libraries? The “Document libraries usage” report provides detailed statistics:
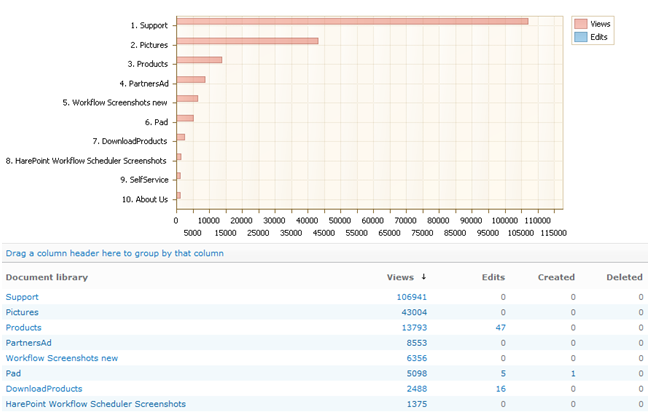
Clicking on any number in the report opens a detailed report showing the corresponding documents. Also, reports on site visits show you from which computer in the company the site was visited.
Lists and list item usage
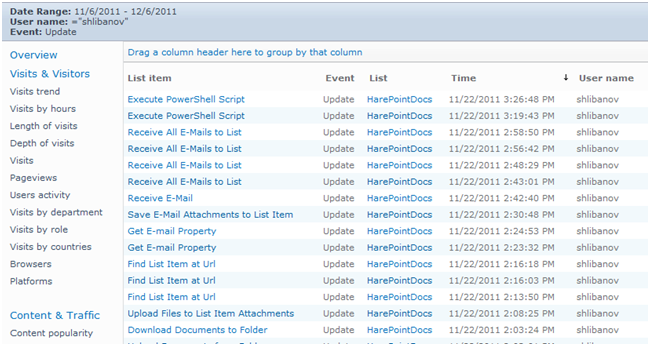
A similar set of reports is available for lists and list items. Thus, the “List items usage” report allows you to obtain the list of all actions with list items for a particular user, or, depending on the filters used to obtain the actions, for all users with a specific element. Thus, in contrast to the audit logs, list items can be seen by the title (if it is available for the given list):
Conclusions
HarePoint Analytics reports save considerable time in incident investigation. They can, in contrast to audit logs, immediately give generalized statistics in tabular and graphical form. This allows you to identify the suspicious activity of users without additional data processing. Together with the data concerning site visits, these reports also allow you to investigate the misuse of other users` accounts and identify the computers from which such addressing was made.




